Description
FakeDaemon
FakeDaemon is your go-to tool for spotting hackers when they try to mess with your system. If you think about it, you can call FakeDaemon a honeypot, which is a cool term in the tech world!
What is a Honeypot?
A honeypot is basically a setup that includes an isolated computer and fake data inside a network. The main idea? To trick those cyber troublemakers into thinking your computer has something valuable they want.
Block Those Hackers
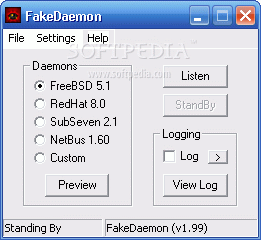
This nifty setup lets you easily collect their IP addresses and add them to your firewall’s blacklist. That way, you can keep them out of your system! FakeDaemon does this by pretending to be busy on certain ports. Plus, its user-friendly interface makes it super quick to set up traps using one of the daemons provided like FreeBSD, RedHat, SubSeven, or NetBus.
How It Works
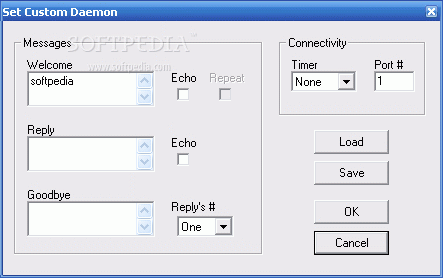
And don’t worry—it’s not about summoning demons or anything spooky! You’re just protecting your data with these setups instead of launching any attacks. You can even create a custom daemon where you can tweak welcome messages, replies, goodbye notes, connection timers, and the ports used.
The Importance of Log Path
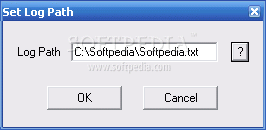
Another crucial part is setting up the Log Path before launching your favorite daemon. This file keeps track of all the sneaky activities it catches and lets you grab any IP address that pops up in its net.
Catch Those Hackers!
The bottom line? FakeDaemon could be just what you need for that honeypot strategy. Once it's running, it might catch hacking IP addresses faster than you can say "butterfly catcher!" You’ll be surprised at how many attacks happen once you connect it to a network—whether it's LAN or the Internet.
If you're looking to download FakeDaemon, check it out at Softpas!
User Reviews for FakeDaemon 1
-
for FakeDaemon
FakeDaemon is a revolutionary tool for detecting hackers. Its simple interface and trap-setting capabilities make it a must-have for cybersecurity.