Description
Boundary
Boundary is an app that really helps those who need to connect to any system, no matter where it is, all while keeping things secure with remote identity checks.
Why Use Boundary?
When you want to connect to a production system sitting behind a private network, it can get tricky. You might run into problems like getting the right access credentials (think SSH keys or VPN info), dealing with network risks, and managing IP addresses in a constantly changing setup.
A Smarter Way to Access Systems
This is where Boundary shines! It brings a fresh approach for handling remote access. At its core, it’s all about trusted identity. This means defining which users can connect and access specific resources. The whole process involves logical systems working together to give the right users access.
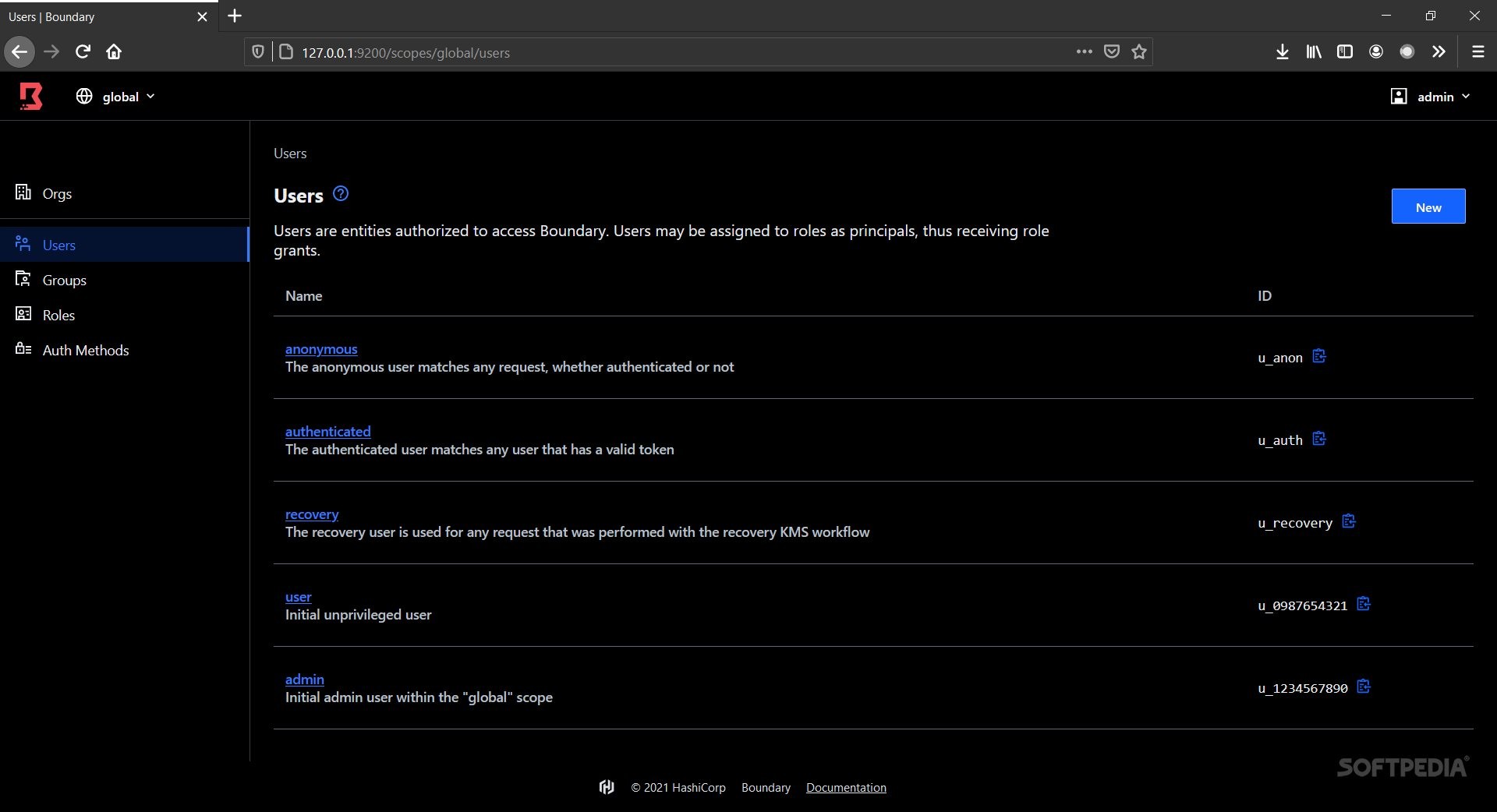
User Management Made Easy
There are some key parts you need to set up: users, which are the individuals trying to connect; and groups, which are collections of users that help manage access. Then there are grants, or permission levels that let users do things in the system.
Straightforward Workflow Steps
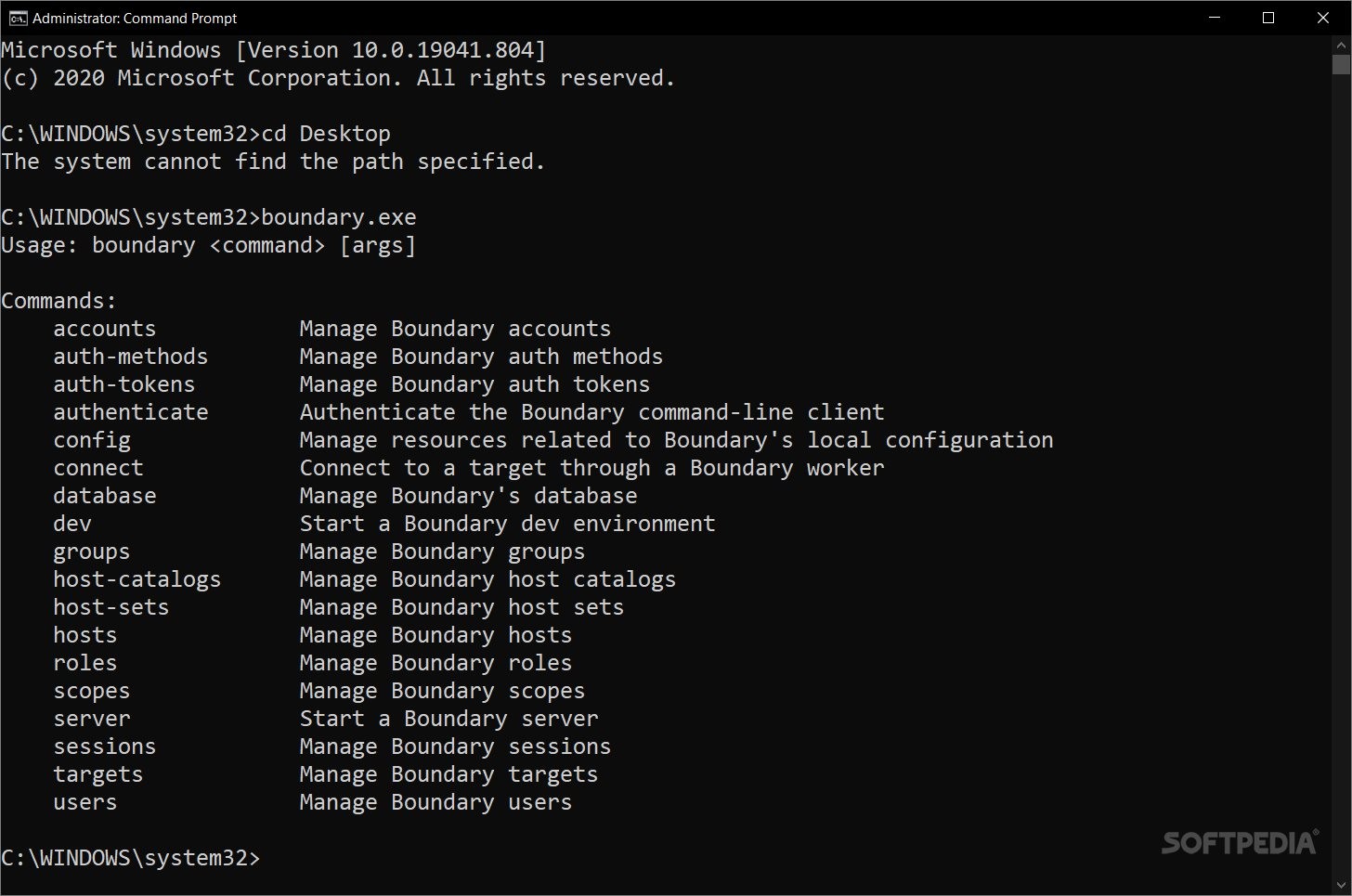
The app's setup follows some easy steps: install and configure your environment, start dev mode (or try the non-dev version), authenticate yourself, get authorized access, and then you’re ready to go!
Full Control Over Sessions
This tool gives you fully-authenticated sessions via TCP (Transmission Control Protocol). Plus, you can keep track of each user's session details—like log time and events—and export this data for analysis later on.
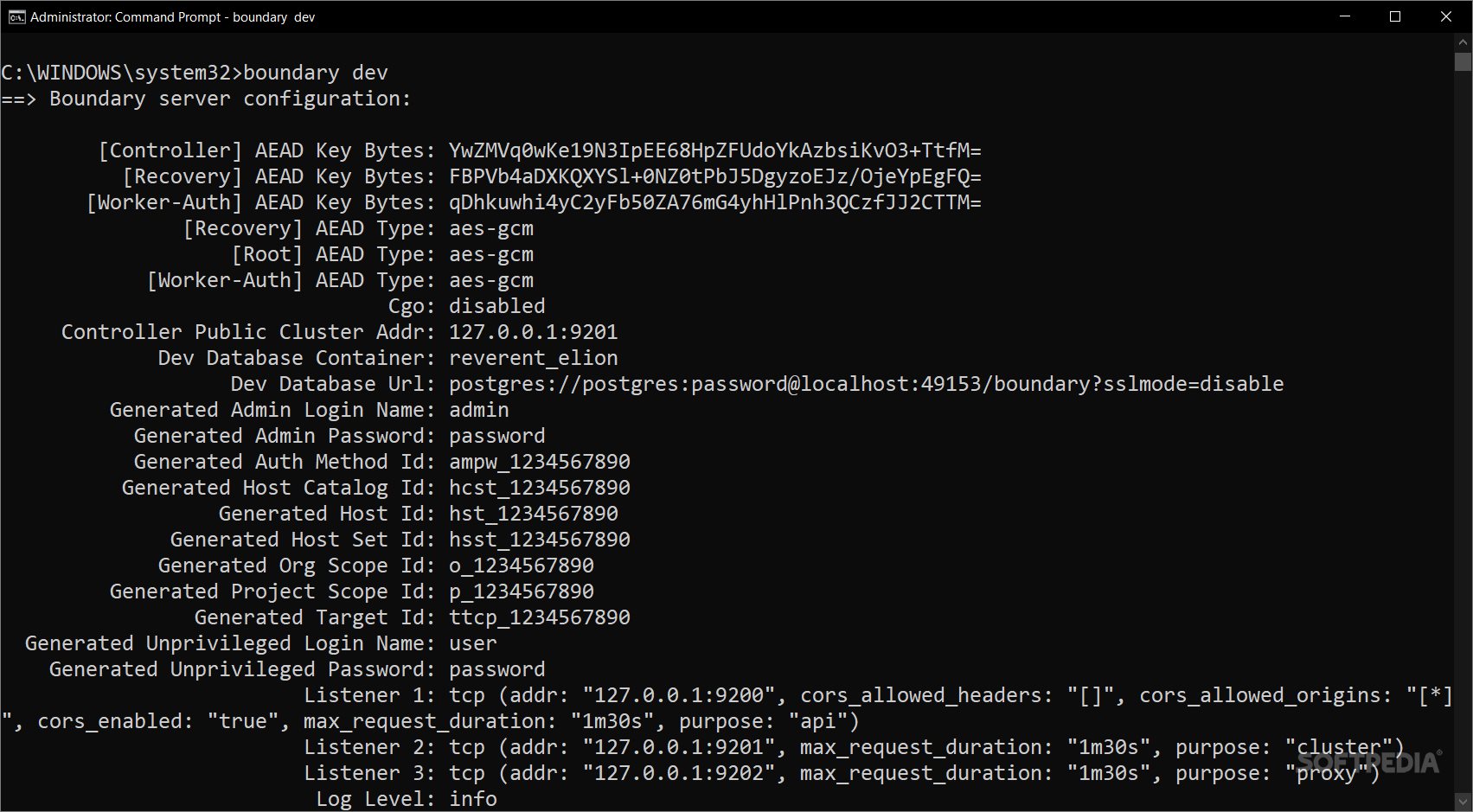
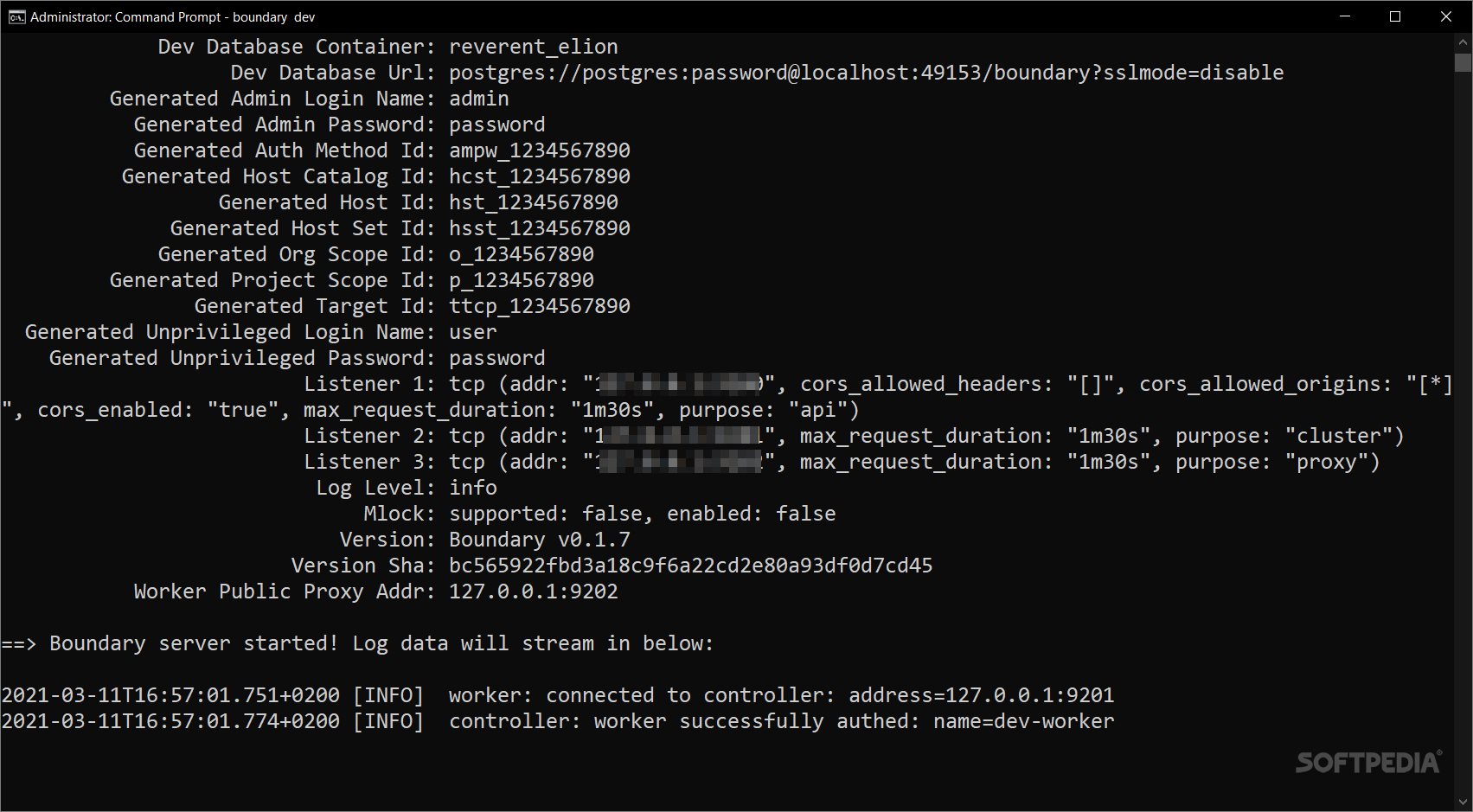
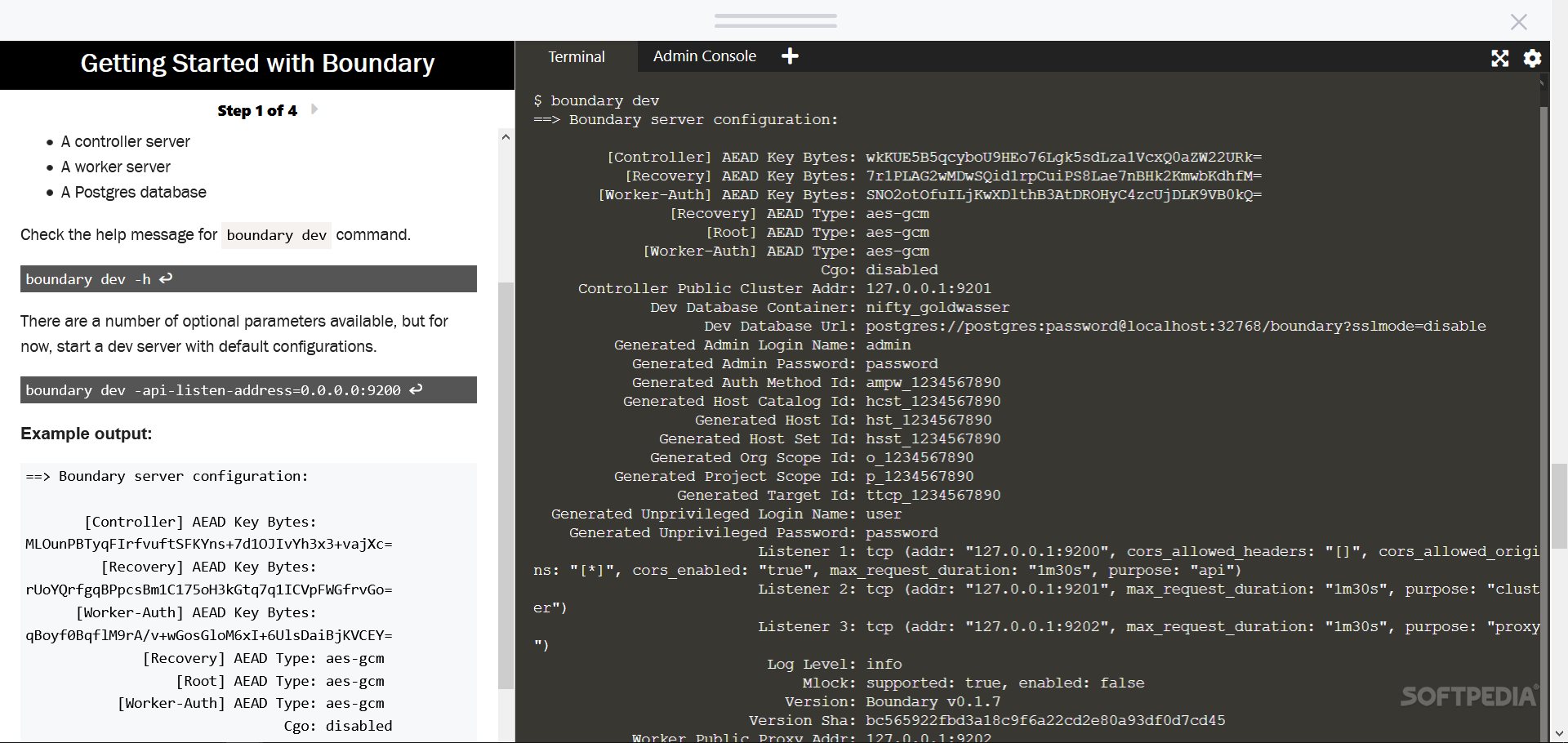
Getting Started with Boundary
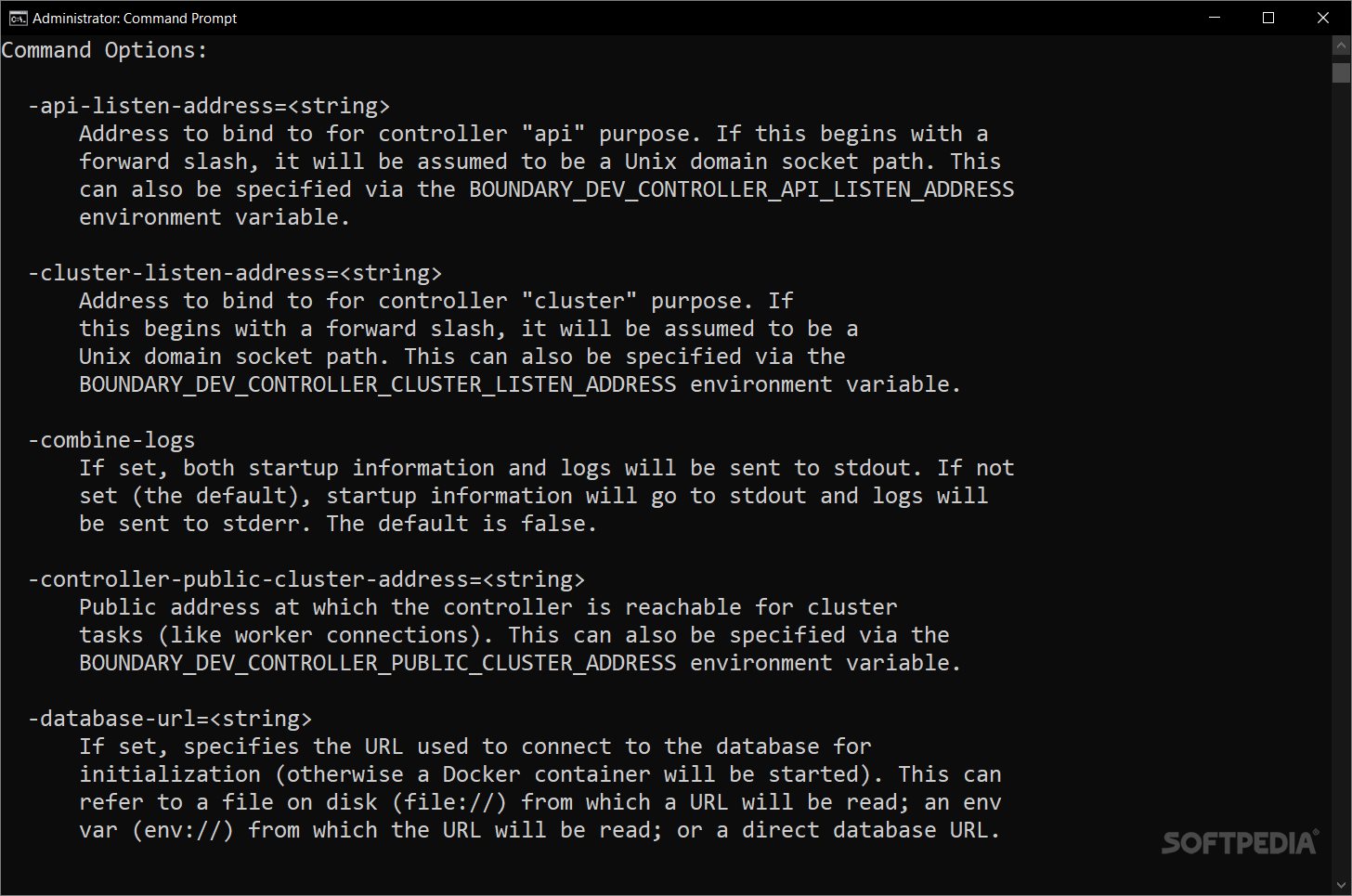
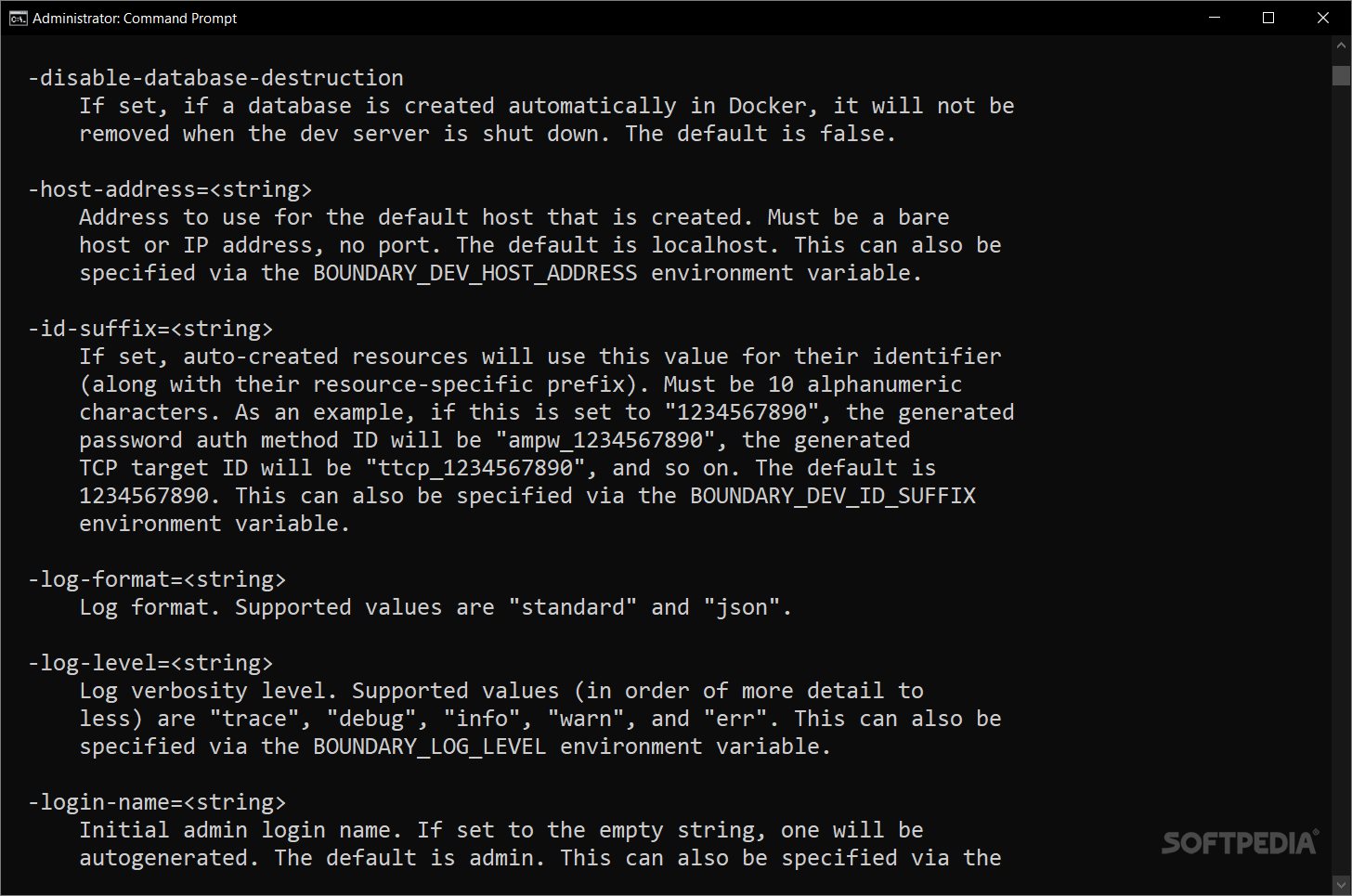
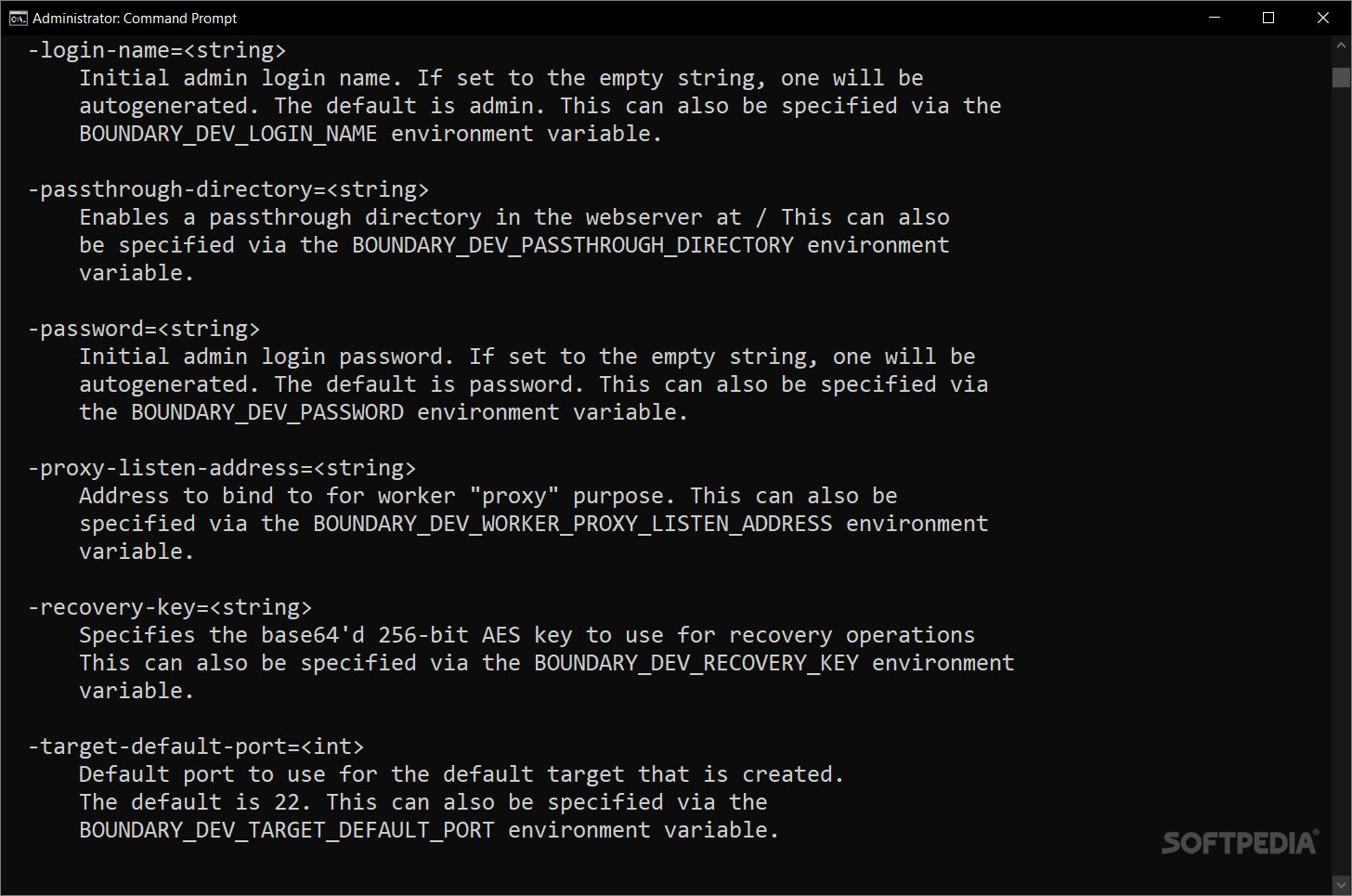
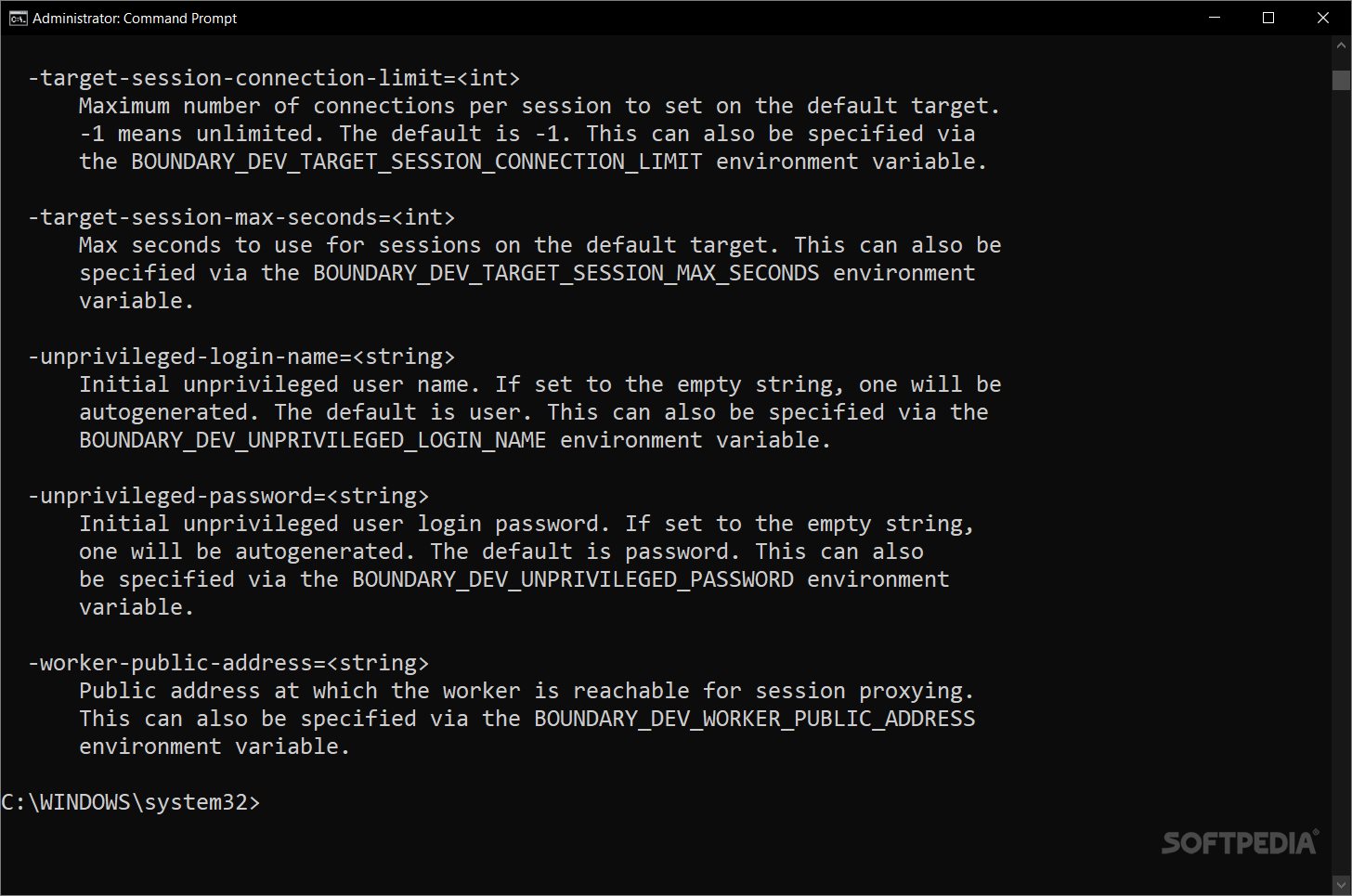
If you're diving into HashiCorp's Boundary in dev mode, make sure you've got Docker set up first. You'll need a way to download and run a Postgres Docker image inside a container too. Also, don’t forget to have the Boundary binary in your PATH. You can place Boundary.exe in C:\\WINDOWS\\system32.
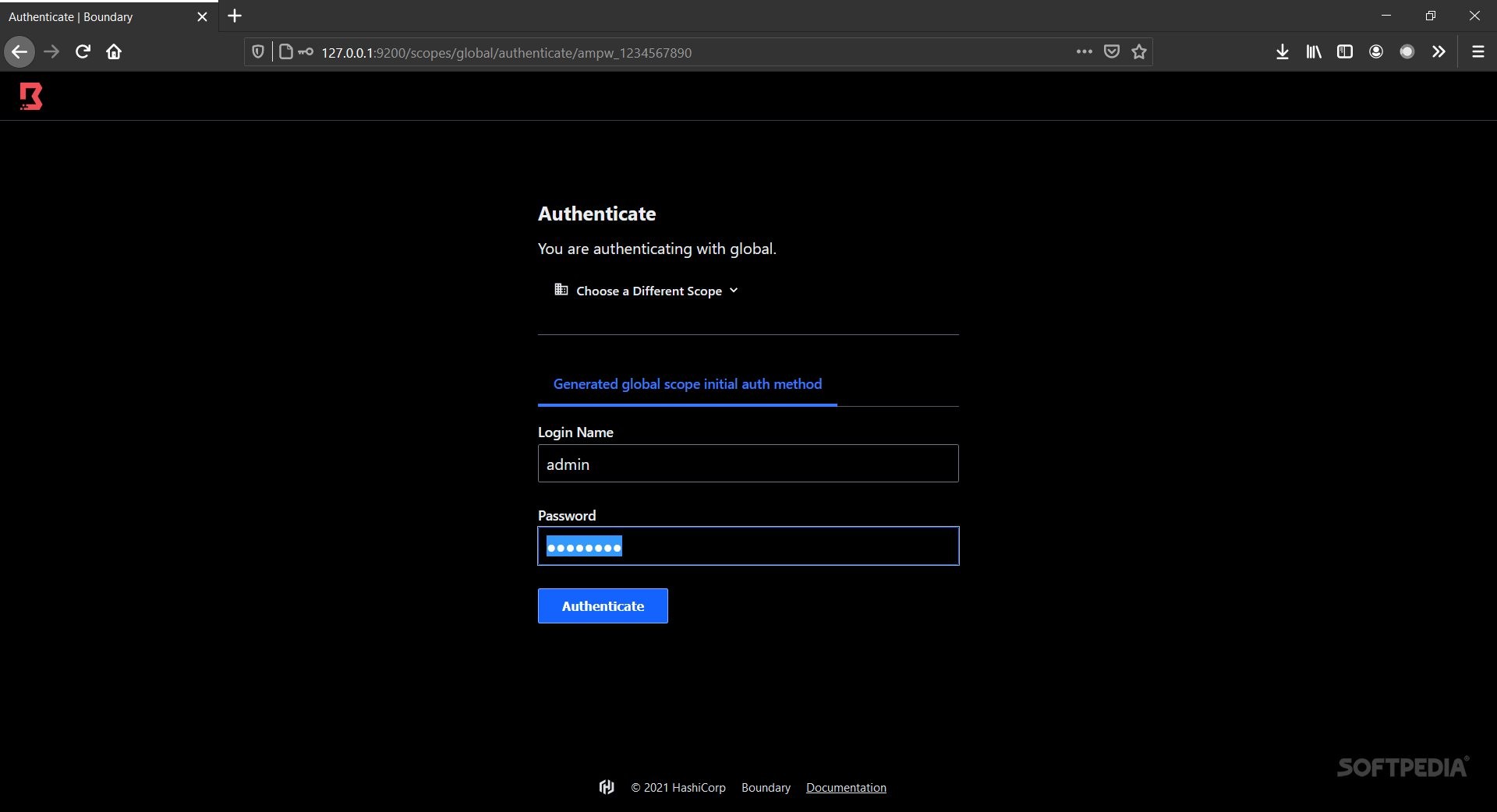
The Next Steps After Configuration
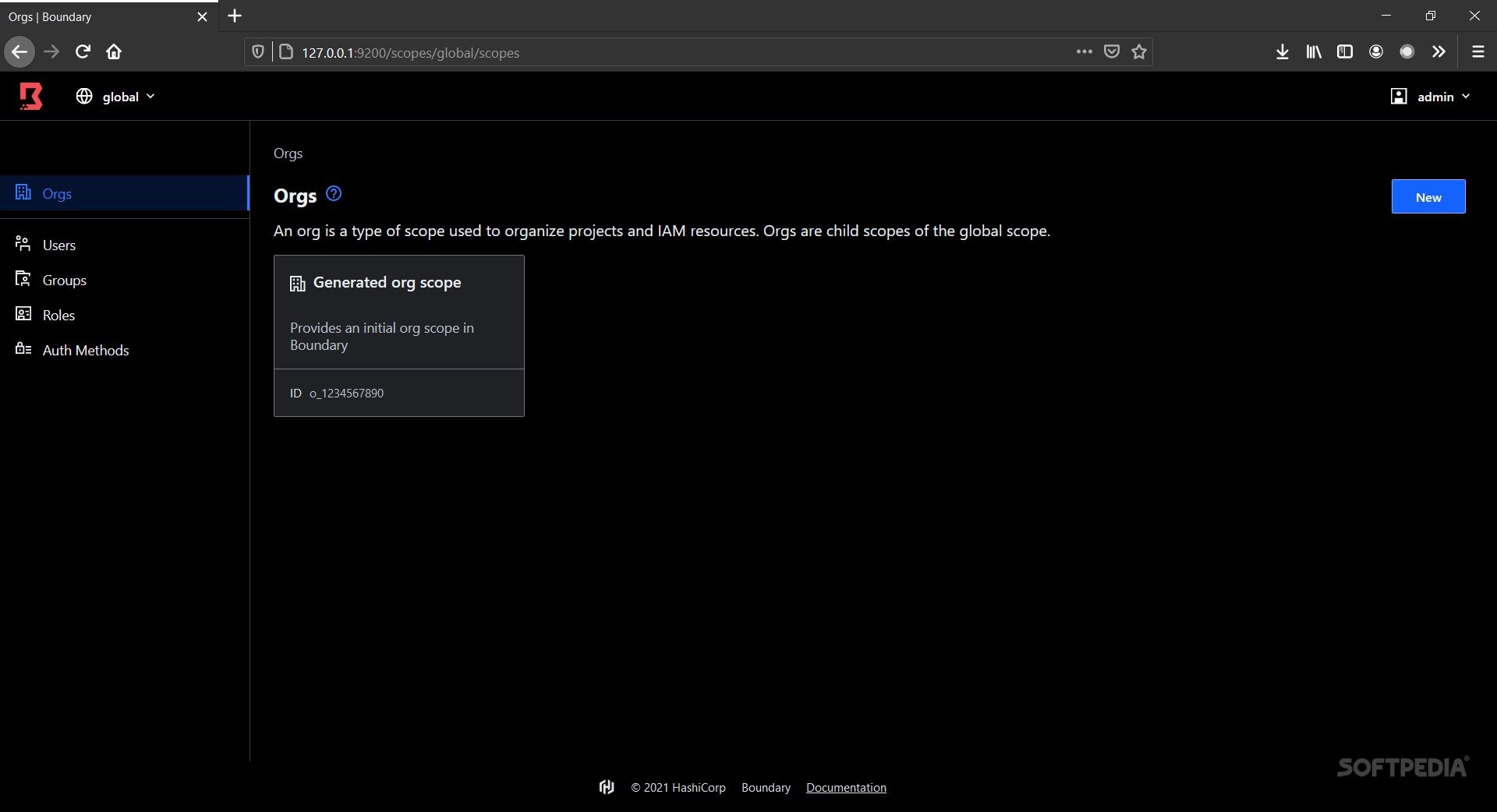
Once you've set everything up, you can check out the tool’s GUI in your browser at http://127.0.0.1:9200, or stick with CLI commands if you prefer! Just remember that while dev mode is great for testing with Postgres databases, it's not meant for production environments.
If you're ready to explore more about this awesome tool and maybe even download it yourself for deeper insights on how it works, check out this link: Download Boundary here!
User Reviews for Boundary 1
-
for Boundary
Boundary simplifies remote access with a focus on secure identity verification. Ideal for managing user groups and permissions effectively.